User Tools
This is an old revision of the document!
Table of Contents
MailCleaner AntiSpam
See also Customizing MailCleaner
See also MailCleaner Quick Guide
See also Zimbra LDAP Directory Notes
See also Exchange E-Mail Security
See also MailCleaner CSF Firewall
See also MailCleaner AntiSpam
See also MailCleaner LetsEncrypt Free SSL
Important Read!: https://medium.com/@victorlclopes/how-to-manage-and-customize-mailcleaner-2020-01-c13bbae12745
User: https://mc.virtualarchitects.com
Support: https://support.mailcleaner.net/
Forum: https://forum.mailcleaner.org/
Traffic Flow: https://www.mailcleaner.net/downloads/Mailcleaner-process.pdf
Windows LDAP Browser: http://www.ldapadmin.org/
Updates
Major Releases: https://www.mailcleaner.net/informations/release.html
![]() Commercial version updates are mostly automatic and can be viewed at Monitoring → Status.
Commercial version updates are mostly automatic and can be viewed at Monitoring → Status.
/root/Updater4MC/updater4mc.sh
![]() You can also perform system updates of the underlying OS:
You can also perform system updates of the underlying OS:
apt update && apt-get dist-upgrade -y && apt-get autoremove -y && apt-get clean && reboot
Firewall
https://support.mailcleaner.net/boards/3/topics/37-customizing-the-mailcleaner-firewall
![]() The built-in firewall and fail2ban for MailCleaner are awkward and unreliable, but cluster-aware. We are using CSF with LFD instead.
The built-in firewall and fail2ban for MailCleaner are awkward and unreliable, but cluster-aware. We are using CSF with LFD instead.
/usr/mailcleaner/bin/mc_mysql -m mc_config
show tables;
select * from external_access;
update external_access set allowed_ip = '192.168.100.0/24' where service = 'configurator';
insert into external_access (service,port,protocol,allowed_ip) values ('configurator','4242','TCP','192.168.130.0/24');
/usr/mailcleaner/etc/init.d/firewall restart
Fail2Ban
![]() Fail2Ban doesn't seem to work correctly, so we use CSF + LFD instead.
Fail2Ban doesn't seem to work correctly, so we use CSF + LFD instead.
Whitelists and Blacklists
Newsletters
Opt Out User
![]() This can only be done by administrators.
This can only be done by administrators.
Management → Users → <address> → Actions → Preferences → Bypass all filtering for this address
Client Administrators
Consolidated Spam Administrator Account
Admin Console
Create a single “spam administrator” user account and add all e-mail aliases that the spam administrator should administer to their Address Group.
User Console
![]() Don't forget to specify
Don't forget to specify Send reports to this address under the User Address Settings and select the checkbox Apply settings to all addresses before saving!
Hotline User
In the admin interface, add a new administrator user:
Configuration → Accesses → New Administrator
Assign the role Hotline.
Assign the domain allowed in Manage Domains.
The new admin user can access the admin interface and see the quarantine of all users of this domain. He has access to all features of the admin interface top section “Management”, but is restricted to the allowed domain.
Add-Ons
Zimbra Integration
Zimbra Admin → Domains → <domain> → General
Mail Domain Aliasing and LDAP
If your MailCleaner alias domains are also aliased on the (Zimbra) mail server, then you can probably use LDAP for address verification and user authentication of all domains.
If you have mail accounts with aliases in multiple domains, you may run into trouble using LDAP address verification. In these cases, it may be necessary to use SMTP address verification for the alias domain(s).
If the domains (and therefore users) are separate on the mail server, you can probably use LDAP for the main (most users) domain and SMTP address verification for the aliased domain(s).
For MailCleaner LDAP usage generally, you probably want to mirror the domain aliasing as used on your Zimbra server.
LDAP Firewall
TCP/389.
Use SSL with Zimbra LDAP as MailCleaner does not support TLS and Zimbra does not support legacy SSL. MailCleaner only supports legacy SSL on port 636, as of January 2021. Official support for TLS is coming in the next version.
![]() Zimbra LDAP uses TCP/389 and TLS internally. Open the Zimbra host firewall to permit your MailCleaner host(s).
Zimbra LDAP uses TCP/389 and TLS internally. Open the Zimbra host firewall to permit your MailCleaner host(s).
![]() A successful connection will not display any prompt. A firewall rejection should be evident.
A successful connection will not display any prompt. A firewall rejection should be evident.
Verify firewall is open from MailCleaner host CLI:
telnet zimbrahost.yourzimbradomain.tld 389
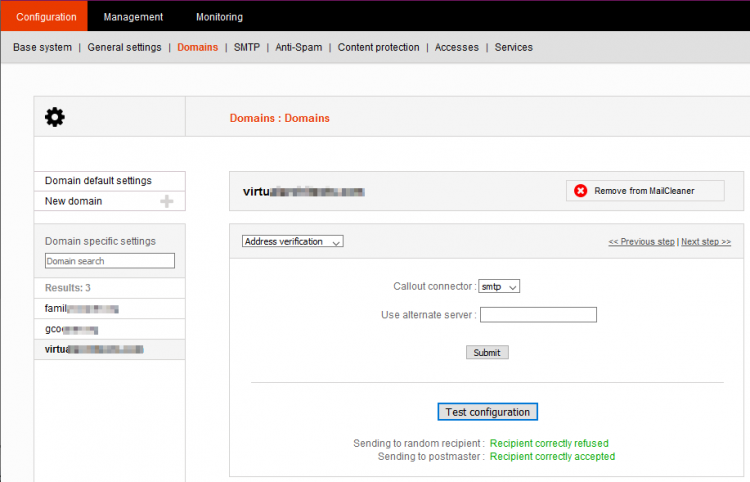
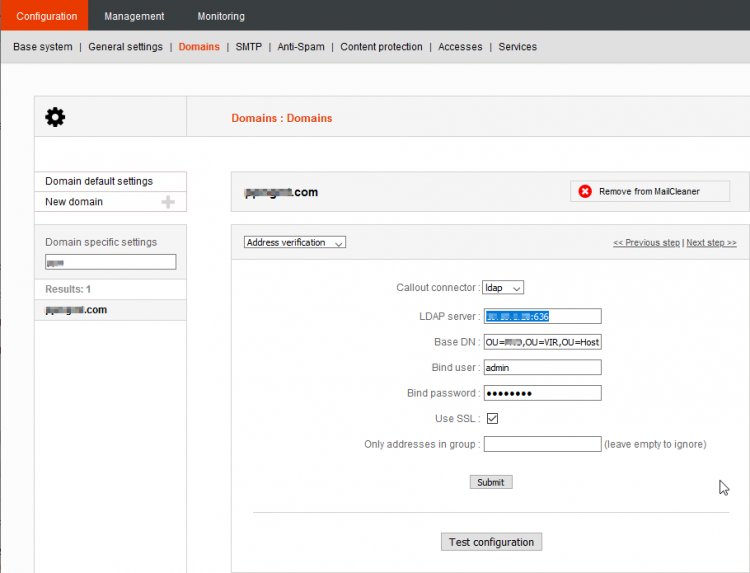
Address Verification
SMTP Address Verification
![]() Like MS Exchange, Zimbra does not reject mail at the SMTP level for non-existent users by default.
Like MS Exchange, Zimbra does not reject mail at the SMTP level for non-existent users by default.
Reject non-existent users at SMTP level for SMTP address verification:
su - zimbra zmprov mcf zimbraMtaSmtpdRejectUnlistedRecipient yes zmprov mcf zimbraMtaSmtpdRejectUnlistedSender yes zmmtactl restart
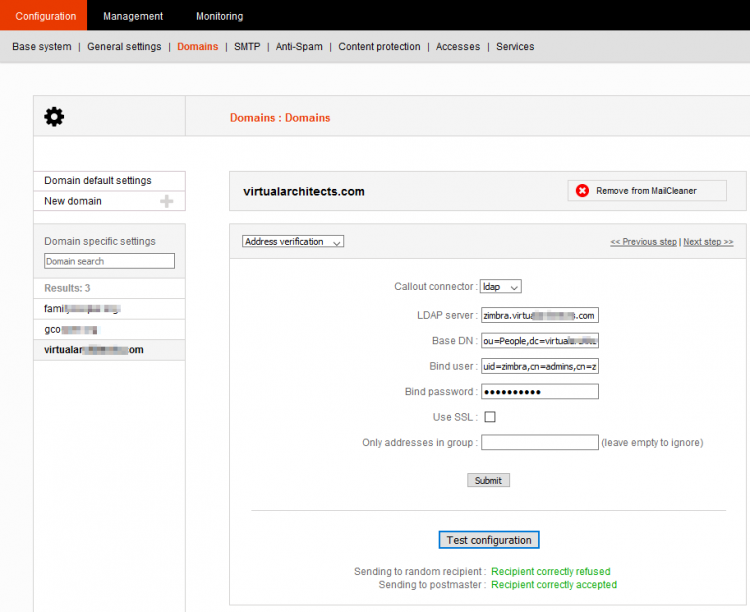
LDAP Address Verification
| Base DN | ou=people,dc=example,dc=com |
|---|---|
| Bind User | from command below |
| Bind Password | from command below |
![]() If your domain has numerous aliases, it is better to use LDAP address verification so aliases are automatically grouped per user.
If your domain has numerous aliases, it is better to use LDAP address verification so aliases are automatically grouped per user.
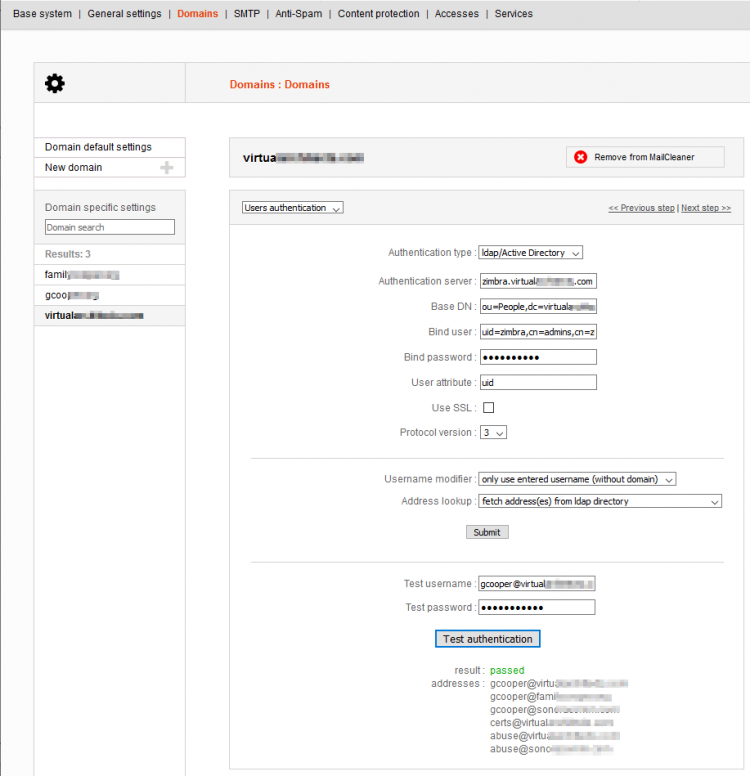
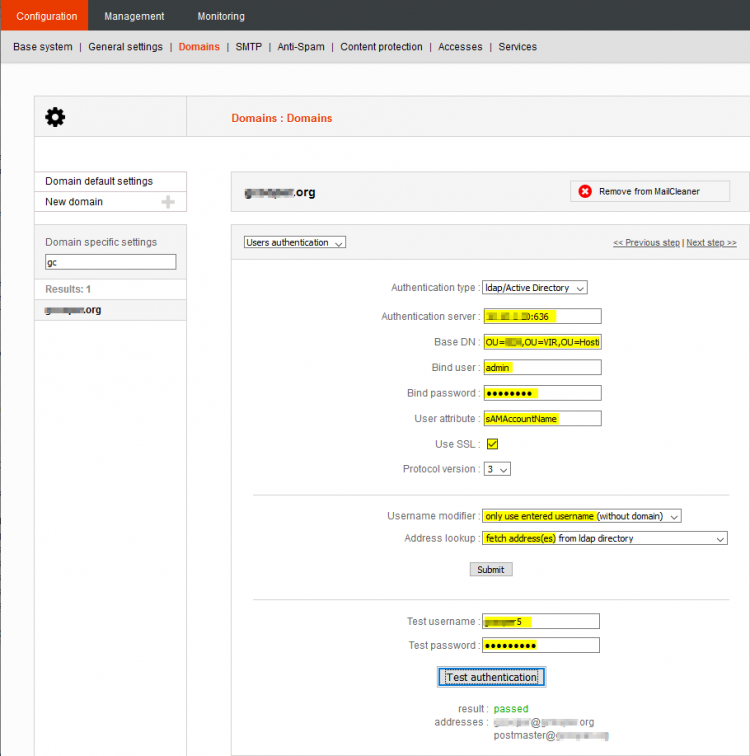
LDAP User Authentication
| Base DN | ou=people,dc=example,dc=com |
|---|---|
| Bind User | from command below |
| Bind Password | from command below |
| Username Modifier | only use entered username (without domain) |
| Address Lookup | fetch address(es) from LDAP lookup |
Per domain at Configuration → Domains → <domain> → Users Authentication:
- MailCleaner Admin UI → Configuration → Domains → <domain> → Users Authentication
- BaseDN:
ou=people,dc=yourdomain,dc=tld - Bind User:
uid=zimbra,cn=admins,cn=zimbra - User Attribute:
uid - Username Modifier:
Use only entered username (without domain) - Address Lookup:
Fetch addresses from LDAP directory
- Test with sample user credentials
Determine Bind User Distinguished Name:
![]() These credentials should probably work for all queries for all domains extant on the Zimbra server.
These credentials should probably work for all queries for all domains extant on the Zimbra server.
su - zimbra zmlocalconfig -s zimbra_ldap_userdn zimbra_ldap_password
Test:
ldapsearch -x -h zimbrahost.yourdomain.tld -D uid=zimbra,cn=admins,cn=zimbra -w <yourpasssword> ldapsearch -x -D "uid=zimbra,cn=admins,cn=zimbra" -w <yourpasssword> -H ldap://zimbrahost.yourdomain.tld -b "ou=people,dc=yourdomain,dc=tld" -s sub 'uid=yourtestuser'
ldapsearch -x -D "uid=search-user,ou=people,dc=example,dc=com" \
-W -H ldap://ldap.example.com -b "ou=people,dc=example,dc=com" \
-s sub 'uid=test-user'
-D - Use bind user "search-user"
-ZZ - Use TLS - place just after -x
-w <password> - Specify password
-W - Prompt for password
-h - LDAP server FQDN
-H - URL of LDAP server. Non-SSL in this case; use "ldaps://" for SSL
-b - The search base
-s - Search scope - i.e. base for base of tree, one for on level down and sub for recursively searching down the tree (can take a while)
Finally the search filter as a non-option argument. In this case we will search for the uid of "test-user"
Virtualmin Integration
Address Verification
Choose SMTP as the Callout Connector.
User Authentication
SpamAssassin
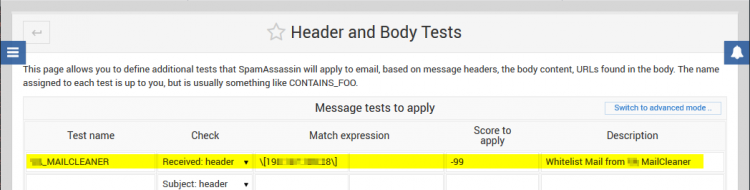
For Virtualmin, we can add a Header Check to give messages from the MailCleaner filter server a 'pass' (whitelisting) through SpamAssassin, while leaving spam and virus filtering enabled for all domains.
This should:
- Permit normal delivery of Quarantine Reports
- Maintain protection from evildoers that try to bybass the DNS MX record (spam filter)
- Allow you to leave spam and virus filtering enabled for all domains
Webmin → Servers → SpamAssassin → Header and Body Tests
Exchange Integration
MailCleaner Documentation: https://support.mailcleaner.net/boards/3/topics/73
User Credentials
![]() Exchange users will use their Active Directory (sAMAccountName) user account credentials. This is probably not their full e-mail address.
Exchange users will use their Active Directory (sAMAccountName) user account credentials. This is probably not their full e-mail address.
Set as Trusted Server
Configure Exchange so that MailCleaner is a trusted internal server where headers are ignored by Exchange filtering:
Get-TransportConfig | fl InternalSMTPServers
Set-TransportConfig -InternalSMTPServers @{Add="<ipaddr>"}
Enable LDAPS
Enable LDAPS on one of your domain controllers:
https://www.youtube.com/watch?v=JFPa_uY8NhY
![]() Reboot the domain controller.
Reboot the domain controller.
Test your LDAPS and firewall connectivity:
telnet your.domain.controller.ip 636
Address Verification
![]() Use LDAP Admin tool to interrogate your specific LDAP directory.
Use LDAP Admin tool to interrogate your specific LDAP directory.
Configuration → Domains → <domain> → Address verification
| LDAP server | ipaddress:port of Exchange LDAP server |
|---|---|
| Base DN | OU=<company>,OU=<reseller>,OU=<platform>,DC=<internal>,DC=<yourdomain>,DC=<tld> |
| Bind user | domain account with permissions |
| Bind password | domain account password |
| Use SSL | select to use legacy LDAP with SSL on port 636 |
User Authentication
Configuration → Domains → <domain> → User authentication
| Username modifier | Only use entered username (without the domain) |
|---|---|
| Address lookup | Fetch address(es) from LDAP directory |
| User attribute | sAMAccountName |
ADUC → Enable Advanced → Attribute Editor
| Test username | Use the Active Directory sAMAccountName, not e-mail address |
|---|---|
| Test password | Test user password |
Troubleshooting
Exim
Exim commands begin like:
/opt/exim4/bin/exim -C /usr/mailcleaner/etc/exim/exim_stage1.conf ...
For example, this will show you the status of queue1:
/opt/exim4/bin/exim -C /usr/mailcleaner/etc/exim/exim_stage1.conf -bp
Change the 1 in the configuration file to 1 2 or 4 where:
| 1 | is the incoming server that accepts messages and forward them to 2 |
|---|---|
| 2 | is the filtering queue; when a message is successfully analyzed it goes to queue 4 |
| 4 | is the outgoing queue that will deliver messages to your domains |
![]() Messages that are NOT for your domains are accepted by queue1 and sent right away to the outside/Internet so queue1 is an outgoing queue for relayed mail.
Messages that are NOT for your domains are accepted by queue1 and sent right away to the outside/Internet so queue1 is an outgoing queue for relayed mail.
More information about this is here: https://support.mailcleaner.net/boards/3/topics/49-exim-queue-management
LDAP
Install ldapsearch on the MailCleaner host:
apt-get update && apt-get install ldap-utils
Packet capture on the Zimbra server:
tcpdump -vv -w ldap.pcap -i eth0 src <ip.of.mail.cleaner>
Spamassassin
![]() Always specify
Always specify siteconfigpath when testing.
Clustered MailCleaner
https://support.mailcleaner.net/boards/3/topics/15-configure-a-loadbalancing-cluster
Use DNS MX records to route mail through the new clustered host.
Use MX record priority to configure load balancing or failover.