User Tools
networking:firewall:windows_troubleshooting
This is an old revision of the document!
Table of Contents
Windows Firewall Troubleshooting
Enable Logging of port dropping packets
- Control Panel → Windows Firewall → Advanced Settings
- Right click on the
Windows Firewall with Advanced Security on Local computer
and select Properties
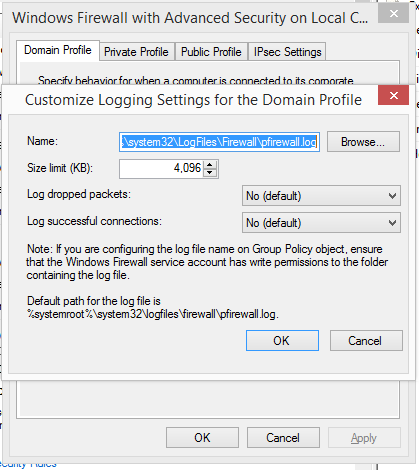
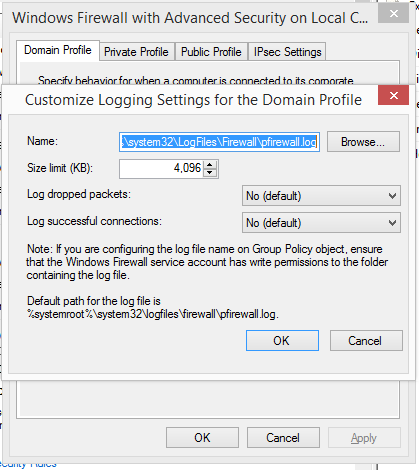
- On the Domain Profile Tab under Logging tab select Customize
- Unordered List Item
- Change Log dropped packets to yes. Note the location of the log in the Name field. Click OK, OK.
- Run the failing process then check the log for which port dropped packets.
One-liner to block evil hosts grep'd from Apache error logs:
for ip in `grep Itau.com.br /var/log/httpd/error_log|egrep -o "client [0-9]+\.[0-9]+\.[0-9]+\.[0-9]+"|sort |uniq|cut -f 2 -d " "`; do iptables -I INPUT -s $ip -j DROP; done
Block Hosts by User Agent String
http://en.linuxreviews.org/HOWTO_stop_automated_spam-bots_using_.htaccess
vim .htaccess
# Block bots by User Agent string SetEnvIfNoCase User-Agent "^Mozilla\/4.0 \(compatible\; MSIE 6.0\; Windows NT 5.1\; SV1\)" bad_bot # Block empty User Agent string SetEnvIfNoCase User-Agent ^$ bad_bot SetEnvIfNoCase User-Agent "^AESOP_com_SpiderMan" bad_bot SetEnvIfNoCase User-Agent "^Alexibot" bad_bot SetEnvIfNoCase User-Agent "^Zyborg" bad_bot <Limit GET POST HEAD> Order Allow,Deny Allow from all Deny from env=bad_bot </Limit>
service httpd restart
networking/firewall/windows_troubleshooting.1458835179.txt.gz · Last modified: 2016/03/24 09:59 by jcooper